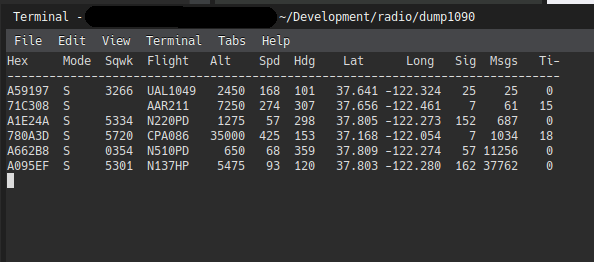
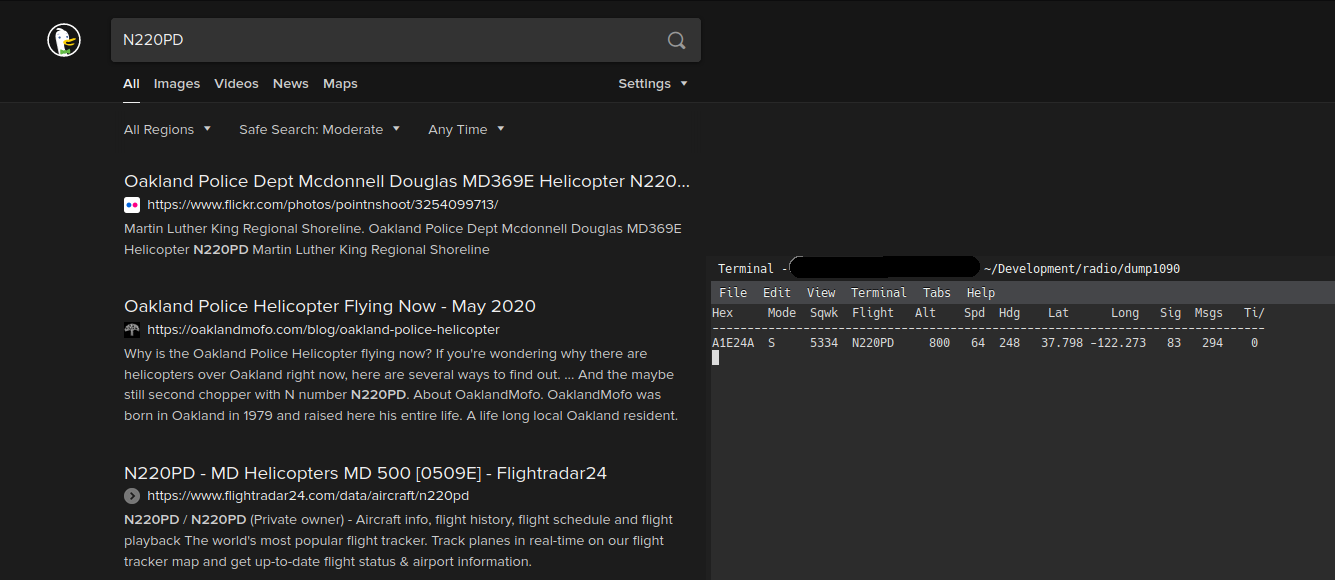
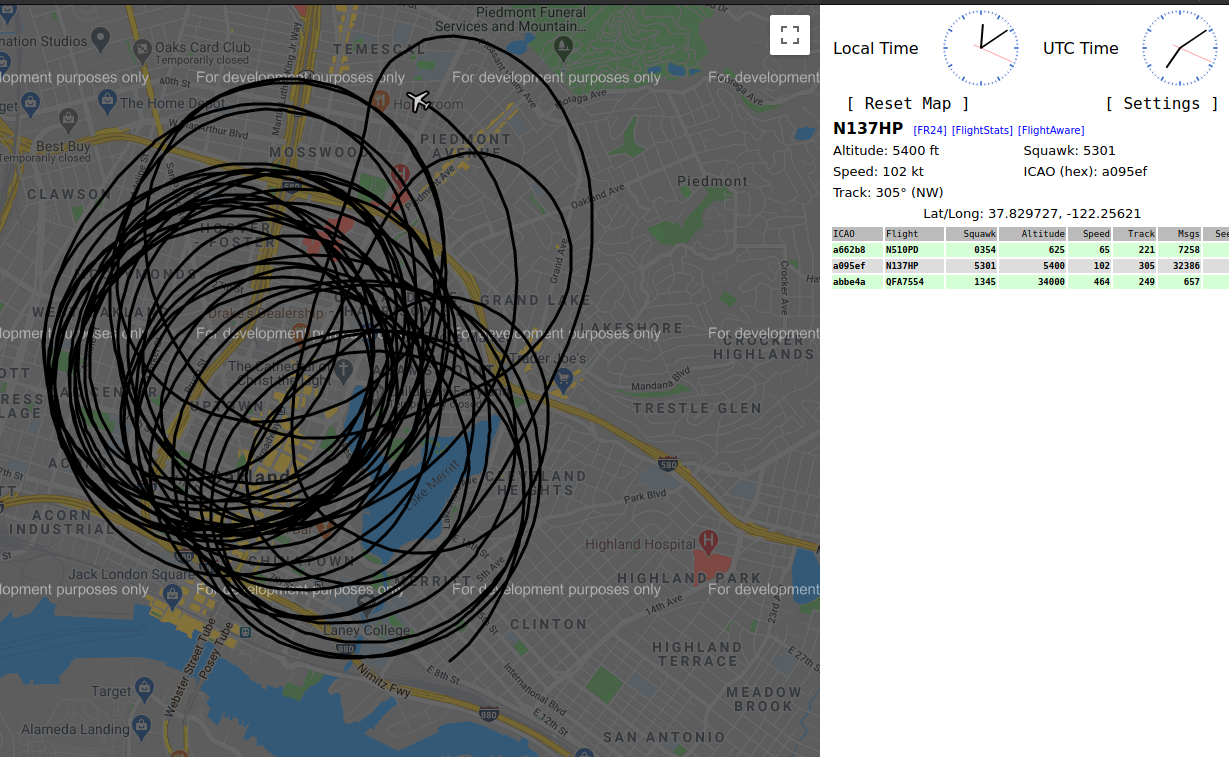
This post is just a quick overview of how I was able to set up a tiny ADS-B listening station during the civil unrest in late May 2020.
For some context, George Floyd was killed nearly a week ago and protesters and opportunistic looters have been in conflict with local police. Over the past few days reports of Predator drones over Minneapolis as well as the near-constant whir of helicopters piqued my interest. Hard to feel like you're participating in civil discourse during quarantine + curfew when you don't use social media!
Automatic Dependent Surveillance - Broadcast or ADS-B is a radio technology used to communicate aircraft positions to air traffic control and other aircraft. This prevents accidents, but also allows for plane spotters to determine what's in the sky. Given that the FAA's requirement for helicopters to include ADS-B as well went into effect on January 1st of 2020, these helicopters can be viewed as well.
Before I go too much further, none of the information that I'm pulling requires any further setup than visiting flightradar24.com. In fact, my observations (as well as those of numerous other contributors) are what power the website. That being said, it's dang cool to set up the system to do this identification.
The first requirement is to acquire an RTL-SDR. This is usually a small USB dongle + an antenna which can be used to receive a wide range of frequencies of interest to hobbyists. I own an RTL-SDR RTL283U. The excellent quick start guide and numerous other blogs contain information of getting the dongle setup and tested on any given system.
*side note* I was able to see the protesters march on to I-580. The police came and arrested the demonstrators fairly quietly. Hopefully I won't need to submit the video to any trials.
In my case, I'm running these tests on Ubuntu so after confirming that
$ rtl_test -t
was still working, I installed an ADS-B decoder called
dump1090. It's
a slick tool that boasts a CLI and a web interface for watching
the paths that identified aircraft are taking. After cloning the
repo to the directory of your choice, simply run make:
$ git clone https://github.com/antirez/dump1090.git
$ cd dump1090
$ make
$ ./dump1090 --interactive
Now the real fun comes with the network mode. Simply pass in the net flag to dump1090 to be presented with a Google Maps overlay with the aircraft plotted on it:
$ ./dump1090 --interactive --net
Finally, if you'd like to share this information with FlightRadar24 and make the data available to the general public, they have packages for Linux for your convenience. Once installed, you can set up your connection by running:
$ fr24feed --signup
$ fr24feed
Another nifty feature of contributing flight data is that you are automatically able to get access to their business plan maps for free. I don't know when I'd need them but hey maybe I'll consider making use of it now.
One of the more interesting flights I managed to catch was this one, KING55, a Hercules flying into San Jose from Seattle.
That's pretty much it for this post. I'll continue gawking from the privileged patio of my apartment, wondering where all of these people (rioters and cops) are coming from and hoping everyone is staying safe and thinking hard about who they vote for this year.
Helpful links to other guides!
- ADS-B Sniffing with the Raspberry Pi and the NooElec 820T Dongle
- ADS-B using dump1090 for the Raspberry Pi
- RTL-SDR Tutorial: Cheap ADS-B Aircraft RADAR (from RTL-SDR.com)
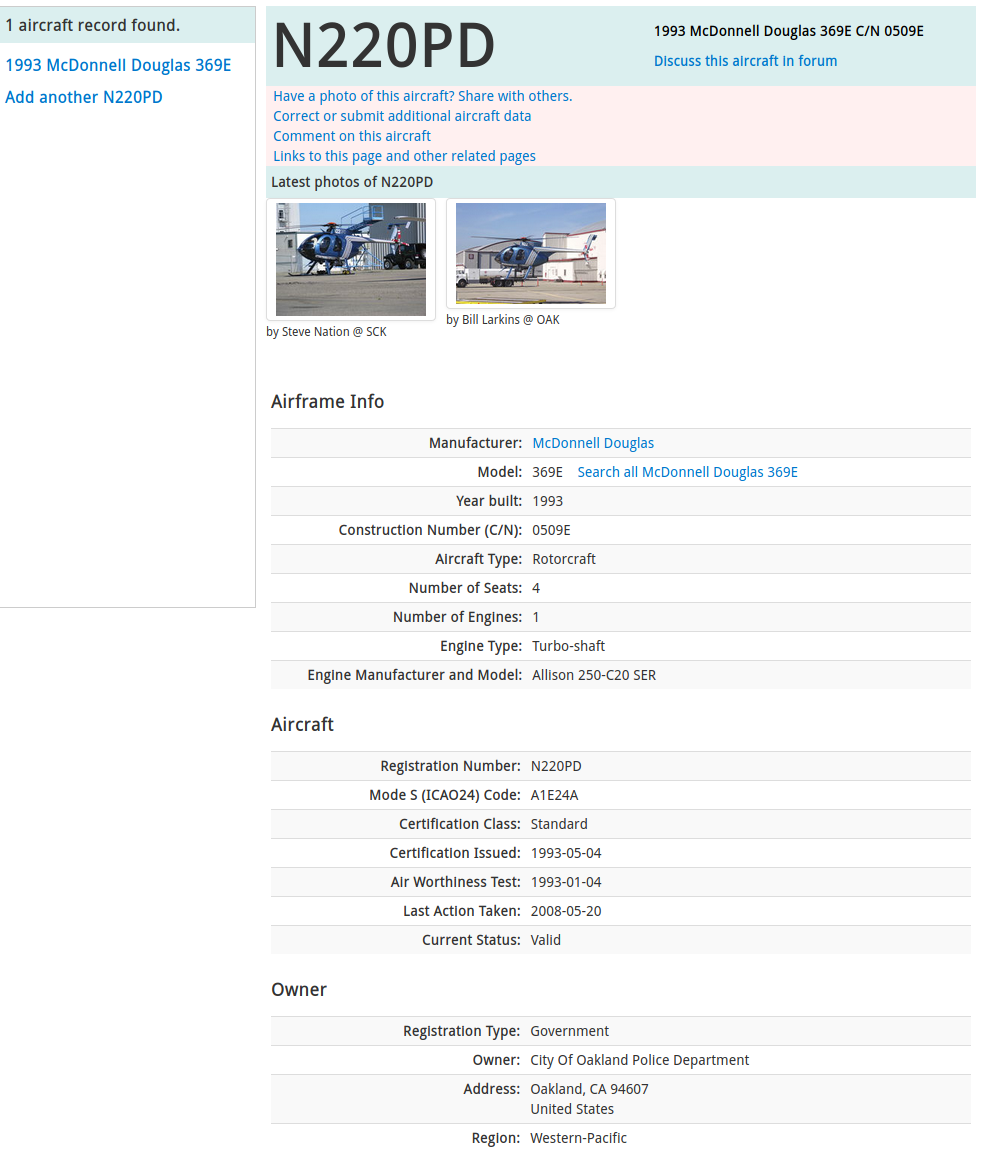
UPDATE: As of ~1am I'm no longer able to see N220PD's flight stats. Sad times. Luckily Airport Data still has me covered.
UPDATE 2020/06/01It turns out that the East Bay Regional Communications System (EBRCS) is running unencrypted P25 trunking. That means using SDR Trunk it's possible to get solid audio from the emergency dispatch system. Thank you to John's Musings for this blogpost tutorial for the easy introduction. Listening to some havoc inside a Macy's right now. Listen Here This player probably won't work but try it anyway: